In general economics, “asymmetric information” refers to information about a transaction in which one party knows more than another party, to the potential benefit of the former at the expense of the latter. An example often occurs when consumers and a business are counter-parties in consumption transactions. Consumers commonly rely on companies to safeguard their personal and company-specific data used in the transaction without explicitly knowing the internal safeguards and standards placed by the data-holding company on their data protection infrastructure (Moore, 2010).
In theory, the risk to corporate reputation and the prospect of breach-related legal judgments and awards or regulatory fines (e.g. under the European General Data Protection Regulation, or GDPR, Directive of 2018) can act as a deterrent against cybersecurity strategies and practices that can lead to a data loss or breach (Farrell, 2016:). In practice, this may not be enough, as the frequency, level, intensity, and complexity of cybercrime continue to grow (Klop, 2016). Crucially, the negative reputational and direct costs of such attacks are increasing over time, generating material shocks to individual companies’ valuations and, potentially, spilling over to broader financial markets.
Not surprisingly, cybersecurity risks are now the focal points of attention among policymakers, regulators, supervisors, and enforcement officials across a range of economic sectors. A key example, and probably the most advanced relative to other sectors, is financial services. This fact is reflected in rapidly expanding regulatory and supervisory efforts to address the key cybersecurity risks from international financial regulation bodies (e.g. the Bank for International Settlements), national legislatures, national central banks and financial regulatory authorities (e.g. the U.S. Federal Reserve and the ECB) as well as industry-own collective representative bodies (e.g. American Banking Association Cyber and Information Security Working Group).
While the growing severity of cybersecurity risks to the global financial system is a matter of consensus, little is known about the systemic channels for cybersecurity contagion across financial markets, especially equity and bond markets. Furthermore, there is no empirical evidence of such systemic contagion in the academic literature, despite repeated references to this phenomenon in regulatory and professional studies. Our paper, “What the Hack: Systematic Risk Contagion from Cyber Events,” forthcoming in the International Review of Financial Analysis, fills this important gap.
We empirically examined the evidence for the unexpected transmission of cybercrime events to company valuations during the period of 2005-2015. Data for all breaches were obtained through analysis of the LexisNexis database, using a range of keywords. As the main hypotheses of this paper, detailed below, deal with the potential for systemic spillovers of cybercrime across financial markets, only publicly traded companies were used in this analysis. We identified a type of cybersecurity breach experienced by the firm, the date of the breach, the date of the breach discovery, the date of public information concerning the breach release, the number of client records affected, and the firm’s market valuation at the time of the breach. Our data represented all 819 publicly disclosed cybersecurity breaches, of which 230 took place with respect to the companies with market capitalization in excess of $1 billion. We then focused on the latter subset of larger companies due to higher informational content of their publicly listed share prices.
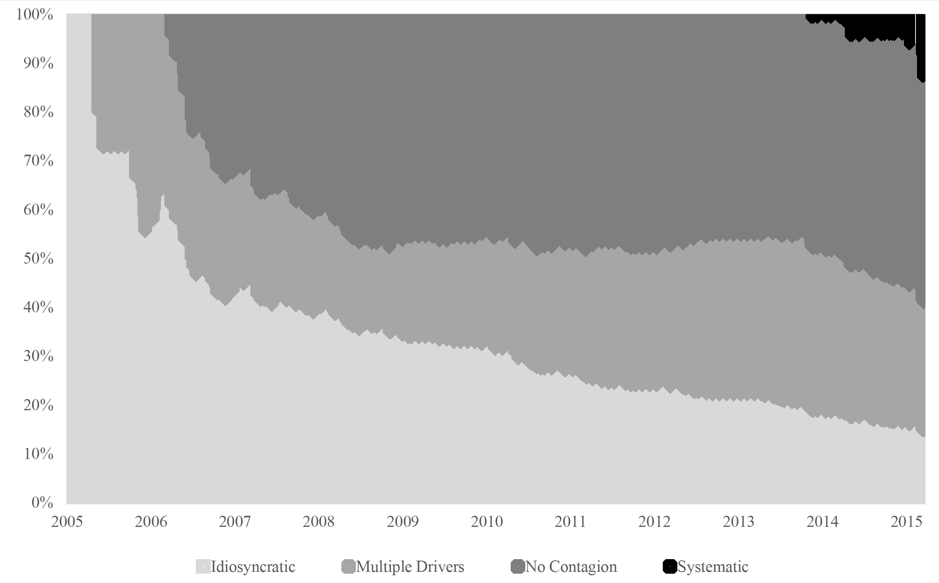
Using GARCH (Generalized Autoregressive Conditional Heteroscedasticity) methods, we show that, starting with 2014, cybercrime events have financial markets impacts that cross exchanges on which the affected firm’s shares are listed, as well as international borders (see Figure below). More specifically, we deploy EGARCH methodology to investigate the stock market volatility of publicly traded companies generated in the immediate aftermath of a hacking or other cybersecurity breach event. The key ways that such spillovers manifest themselves publicly, in our opinion, are: 1) changes in equity prices for the affected firms (own impact), consistent with evidence shown by our analysis of cumulative abnormal returns or losses that arise in the aftermath of the cybersecurity breach; 2) spillover to other companies linked to the affected firm through share listings on the same exchange and; 3) spillover from the affected firm to other exchanges.
Figure: EGARCH calculated contagion type stemming from cybercrime event (2005-2015)
Source: Corbet and Gurdgiev (2019a)
In effect, trading or portfolio links, or institutional structures such as international subsidiaries, help propagate risk, including for cybersecurity risk spillovers. This is the first paper in the literature on cybersecurity and finance to provide conclusive evidence and empirical tests for how cybersecurity risk is transmitted from one company to others in related sectors or markets.
Beyond the systemic nature of the threat, the magnitude of costs and disruptions imposed on economies by cyber-attacks is growing. According to EU authorities (Stearns, 2016), cybersecurity incidents resulting from human error, technical failures, or cyber attacks cause annual losses of 260-340 billion euros. Since these estimates exclude the impact of potential contagion from the directly-affected companies to broader markets, these figures are likely to severely underestimate the true extent of the cybersecurity-breach costs.
We also show that hacking has become the most prevalent form of cybercrime, with incidents becoming more frequent, more severe in their impact on equity valuations and volatility, and more sophisticated. The contagion effects of hacking are far more pronounced than cybercrime relating to employee data releases or the physical theft of data. Data that have been lost or stolen through loss or theft of physical devices present strong evidence of contagion effects, but there have been quite a few occurrences since 2012, indicating that companies may be allocating more resources to stopping this type of cybercrime at the source.
Our results support the importance of immediate regulatory intervention to mitigate the effects of cybercrime. Cybercriminals appear to be more sophisticated than those who monitor and regulate cybersecurity systems of larger companies. Some regulatory strategies are beyond the scope of this paper, but are the subject of our second paper (Corbet and Gurdgiev, 2019b).
REFERENCES
Corbet, S. and Gurdgiev, C. (2019a). What the Hack: Systematic Risk Contagion from Cyber Events. Forthcoming in International Review of Financial Analysis, Fall 2019, https://www.journals.elsevier.com/international-review-of-financial-analysis. Pre-print version of the paper is available via SSRN: https://ssrn.com/abstract=3033950 or http://dx.doi.org/10.2139/ssrn.3033950.
Corbet, S. and Gurdgiev, C. (2019b) An Incentives-Consistent Mechanism for Corporate Cyber-Governance Enforcement and Regulation. Forthcoming as Chapter 8 in “Emerging Risks in Finance: Ecological, Societal, and Technological Challenges“, eds. Thomas Walker, Dieter Gramlich, and Mohammad Bitar, and Pedram Fardnia. Palgrave Studies in Sustainable Business, Palgrave Macmillan, November 2019.
Drinkwater, Doug (2016). Does a data breach really affect your firm’s reputation? CSOOnline, January 7, 2017: http://www.csoonline.com/article/3019283/data-breach/does-a-data-breach-really-affect-your-firm-s-reputation.html.
Farrell, Scott (2016). Big Hack Attack: Protecting Corporate Reputation and Brand Value in the Wake of a Data Breach, The Public Relations Strategist, Summer 2016, http://apps.prsa.org/Intelligence/TheStrategist/Articles/view/11571/1129/Big_Hack_Attack_Protecting_Corporate_Reputation_an#.WSR22BPyv_8.
Klop, Marloes (2016). “Cybercrime and Corporate Reputation: Business, Government, and Public Perspectives”, IPSOS MORI, October 2016, https://www.ipsos.com/sites/default/files/2016-11/Perceptions_of_Cybercrime_18.10.2016.pdf.
Moore, Tyler (2010). Introducing the Economics of Cybersecurity: Principles and Policy Options. Proceedings of a Workshop on Deterring Cyber Attacks: Informing Strategies and Developing Options for U.S. Policy http://www.nap.edu/catalog/12997.html source: https://www.nap.edu/read/12997/chapter/1 accessed http://static.cs.brown.edu/courses/csci1800/sources/lec27/Moore.pdf.
Stearns, J., 2016. European Union’s First Cybersecurity Law Gets Green Light, July 6, 2016, Bloomberg. https://www.bloomberg.com/news/articles/2016-07-06/european-union-s-first-cybersecurity-law-gets-green-light.
This post comes to us from professors Shaen Corbet at Dublin City University and Constantin Gurdgiev at Middlebury Institute of International Studies at Monterey and Trinity Business School, Trinity College, Dublin. It is based on their recent paper, “What the Hack: Systematic Risk Contagion from Cyber Events,” available as a working paper here.
 Sky Blog
Sky Blog