The U.S. Securities and Exchange Commission (SEC) recently identified incidents in which top executives sold shares before disclosing to the public negative information about cyberattacks. For example, the former chief information officer of Equifax, Jun Ying, exercised his stock options and sold nearly $1 million in shares about a week before Equifax disclosed the hack of its database in September 2017, gaining $480,000. Equifax stock dropped over 30 percent after news of the data breach became public. Motivated by the SEC’s concerns, we examine the relation between insider trading and corporate disclosure policies around cyberattacks.
When a cyberattack with material negative consequences occurs, security regulations require companies to disclose information on the event to the public, as in other incidents with material negative effects. Executives can opportunistically sell shares (or avoid buying shares or granting stock options) before disclosing information on cyberattacks to the public. However, they are unlikely to trade on private information that the firm intends to disclose. Disclosure of the negative information will expose and label preceding sales as insider trading, and executives will not sell shares if they wish to avoid the legal ramifications of insider trading. In some cases, however, firms withhold information and do not disclose the cyberattack to investors; and if the firm chooses to withhold information on the cyberattack, insiders’ sales of shares are less likely to be identified as insider trading.
We predict that the likelihood of insider trading is higher for firms that withhold the information than for firms that voluntarily disclose it. To test this prediction, we identify companies that were attacked and distinguish between those attacked companies that disclosed information on the attack and those that withheld information on the attack, but parties outside the company later discovered the attack. For the subsample of cyberattacks that companies voluntarily disclosed between 2010 and 2015, we find no significant insider trading in the days before the disclosure. However, for cyberattacks about which information was withheld from investors, and parties outside the company later discovered them, we find insiders sold shares after the cyberattacks and before investors learned about these attacks. Moreover, we find top officers, who were more likely to be aware of the cyberattack and influence the decision regarding whether to disclose it, made the insider sales, whereas other insiders did not sell stocks.
Finally, we find insider trading after withholding information is less likely in firms incorporated in U.S. states with stricter disclosure requirements on data breaches. Certain states require companies to disclose cyberattacks to the state attorney general. For example, companies incorporated in California must notify the California attorney general about data breaches that affect private information of more than 500 customers or individuals. We find managers are less likely to withhold information on cyberattacks and trade on the information in states that require such additional disclosure. The clear requirement to disclose a breach to state agencies marks that breach as a significant event, on which insiders are less likely to trade before its disclosure due to litigation risk. When disclosure requirements are less strict, insiders trade after withholding information on the cyberattack.
Our sample includes 192 cyberattacks involving 120 publicly traded companies between 2010 and 2015, of which 42 firms had more than one cyberattack. We divide the sample into three groups. The first group (101 cases), denoted as Disclosing, includes cyberattacks that the attacked firm disclosed before an outsider discovered it. The second group (33 cases), denoted as Withholding, are cyberattacks that the attacked firm had not disclosed for at least two days after it learned of its occurrence and a party outside the firm consequently discovered the attack. The third group (58 cases) includes Immaterial cyberattacks. Firms are not required to disclose attacks with immaterial effects, and this group includes cyberattacks that an outsider discovered, but the firm communicated that the attack caused no material damage.
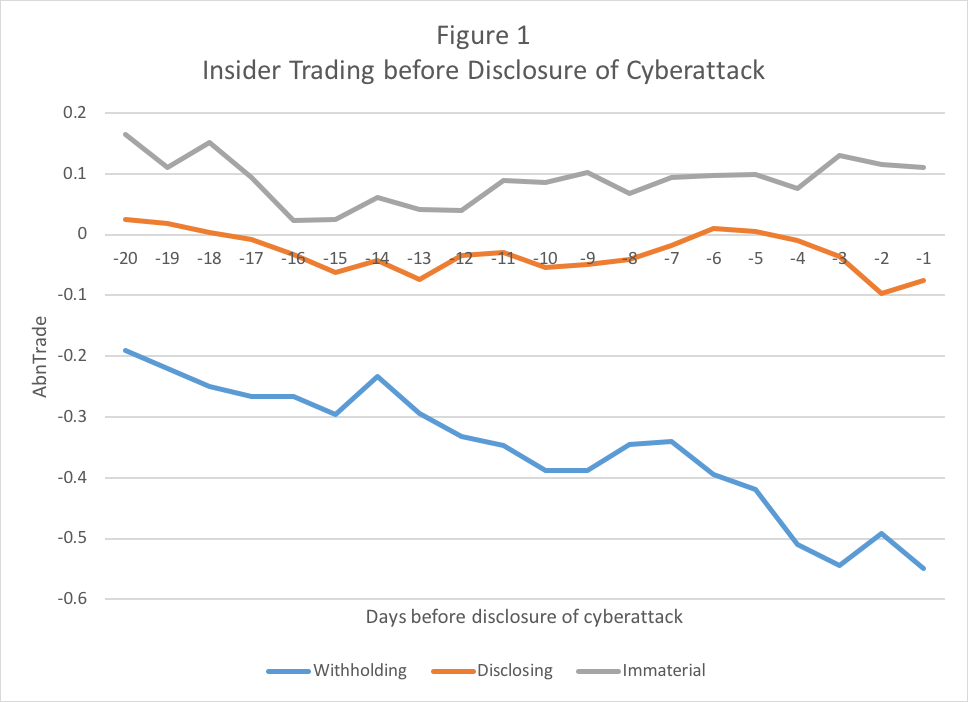
Figure 1 shows daily abnormal insider trading in the 20 days before the discovery of the cyberattack. Initially, we compute, for each firm/day, Trade (t-9, t) for t = {-20, -1}. For example, for day t = -2, we compute for each firm Trade (-11, -2). Similarly, for day t = -3, we compute Trade (-12, -3). Then, we compute abnormal daily net trade:
AbnTrade (t-9, t) = Trade (t-9, t) – Trade (-120, -60).
Figure 1 presents the abnormal daily net trade for the 20 days before the attack for the three subsamples: Withholding, Disclosing, and Immaterial. As the figure shows, net trading becomes more negative for Withholding companies. Insiders in Withholding companies sell more shares as the discovery of the cyberattack approaches, whereas the pattern for Disclosing and Immaterial subsamples is stable around zero abnormal net trading.
We also examine insider sales immediately after managers became aware of the attack. As indicated above, we have the date managers learned of the attack for withholding cases. We calculate abnormal insider trading after the date managers learned of the attack, τ, relative to trading in the preceding month: AbnTrade (τ, τ +30) = Trade (τ, τ +30) – Trade (τ -30, τ -1), and find significant trading in the withholding cases.
The primary contribution of our study is that it links corporate disclosure policy to insider trading. Specifically, we demonstrate the effect of stricter disclosure rules on insider trading, and show that when managers are clearly required (by state law) to report cyberattacks, they are less likely to trade on the information before disclosing it. However, when disclosure threshold depends more on managers’ discretion, managers are inclined to trade on withheld information.
This post comes to us from professors Eli Amir and Shai Levi at Tel Aviv University’s Coller School of Management and Tsafrir Livne at the University of North Carolina’s Kenan-Flagler Business School. It is based on their recent paper, “Insider Trading and Disclosure: The Case of Cyberattacks,” available here.
 Sky Blog
Sky Blog